Match the continuous auditing alarms to flag the fraud schemes – Matching continuous auditing alarms to flag fraud schemes sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset.
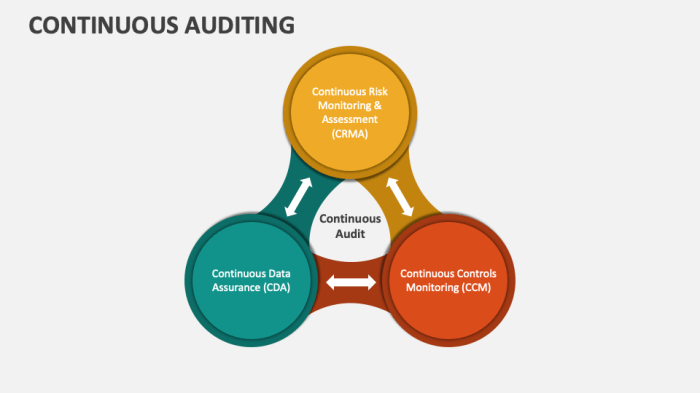
Continuous auditing, a revolutionary approach to fraud detection, empowers organizations to stay vigilant against fraudulent activities. By leveraging continuous auditing alarms, organizations can proactively identify and mitigate fraud schemes, safeguarding their financial integrity and reputation.
Fraud Detection Strategies

Continuous auditing is a proactive approach to fraud detection that involves ongoing monitoring of financial and operational data to identify anomalies and potential risks. Continuous auditing alarms can be configured to flag specific patterns and behaviors that may indicate fraudulent activities, enabling organizations to respond quickly and effectively.
By leveraging continuous auditing alarms, organizations can enhance their fraud detection capabilities and improve their ability to prevent, detect, and respond to fraudulent schemes.
Alarm Configuration and Monitoring

Configuring Continuous Auditing Alarms
Configuring continuous auditing alarms involves defining the specific criteria and parameters that will trigger an alarm when certain conditions are met. Key parameters to consider include:
- Transaction thresholds
- Unusual patterns
- High-risk vendors or customers
- Employee access levels
Ongoing Monitoring and Fine-Tuning, Match the continuous auditing alarms to flag the fraud schemes
Once alarms are configured, it is essential to monitor their performance and make adjustments as needed. Ongoing monitoring helps ensure that alarms remain effective in detecting fraud and that they are not generating false positives or missing potential red flags.
Common Fraud Schemes and Alarm Mapping
| Fraud Scheme | Alarm Description | Triggering Conditions |
|---|---|---|
| Billing Fraud | Identifies unusual billing patterns, such as inflated invoices or unauthorized charges | – Significant increase in billing amounts
|
| Expense Reimbursement Fraud | Detects fraudulent expense claims, such as duplicate submissions or inflated expenses | – High-value expense claims
|
| Procurement Fraud | Flags suspicious procurement activities, such as vendor overcharging or bid rigging | – Contracts awarded to vendors with poor performance records
|
| Payroll Fraud | Identifies anomalies in payroll processing, such as ghost employees or inflated salaries | – Large increases in payroll expenses
|
Case Studies and Best Practices: Match The Continuous Auditing Alarms To Flag The Fraud Schemes
Case Study: Detecting Billing Fraud Using Continuous Auditing Alarms
A manufacturing company implemented continuous auditing alarms to monitor billing transactions. The alarms were configured to flag invoices that exceeded a certain threshold or were submitted by new vendors. This approach enabled the company to identify and investigate a billing fraud scheme involving inflated invoices from a fraudulent vendor.
Best Practices for Implementing Continuous Auditing Systems
- Establish clear fraud detection objectives.
- Identify key risk areas and potential fraud schemes.
- Configure alarms based on relevant criteria and parameters.
- Implement ongoing monitoring and fine-tuning of alarms.
- Train staff on fraud detection techniques.
FAQ Explained
What is the significance of continuous auditing in fraud detection?
Continuous auditing plays a pivotal role in fraud detection by providing real-time monitoring and analysis of financial transactions and operations. This enables organizations to promptly identify anomalies and suspicious patterns that may indicate fraudulent activities.
How do continuous auditing alarms contribute to flagging fraud schemes?
Continuous auditing alarms are designed to trigger alerts when specific predefined conditions or thresholds are met. By configuring these alarms to align with known fraud schemes, organizations can automate the detection process, ensuring timely identification and response to potential fraudulent activities.
What are some common fraud schemes that can be flagged using continuous auditing alarms?
Continuous auditing alarms can be tailored to flag a wide range of fraud schemes, including but not limited to: unauthorized transactions, vendor fraud, expense reimbursement fraud, and payroll fraud. By mapping alarms to specific fraud schemes, organizations can enhance their ability to detect and prevent these fraudulent activities.